Experts predict a 50%-70% chance of quantum computers cracking current cryptosystems within 5 years unless the latest cryptographic controls are put in place.
0
%
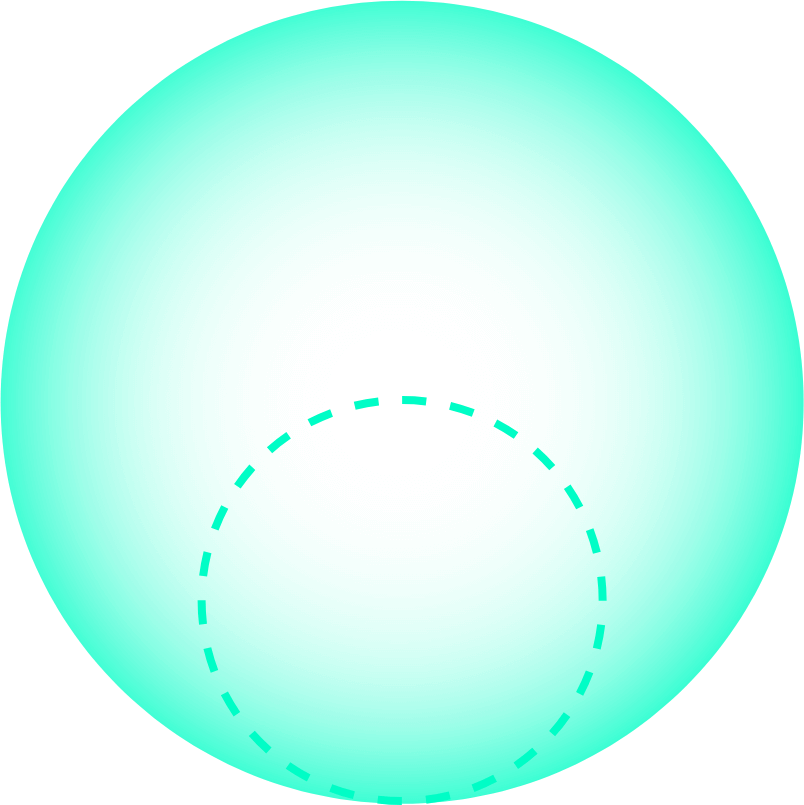
0
%
Provides continuous surveillance and monitoring of cryptographic communications for every session across your organization’s entire IP infrastructure.
Employs sophisticated domain name and attacker intelligence to preemptively counter malicious communications from your organisation.
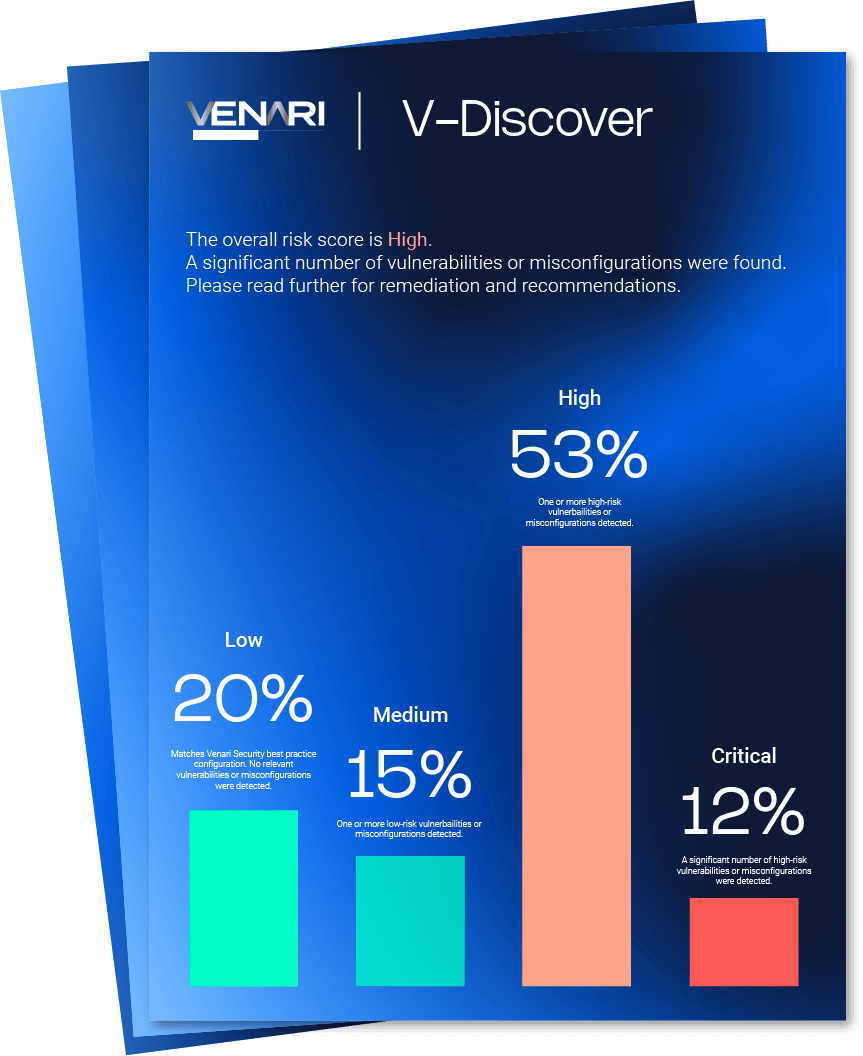
Access your risk profile, ensure compliance with NIST, NCSC, NSA, Venari Security and other benchmarks.
Gain visibility into your company’s cryptographic attack surface and leverage insights against existing industry benchmarks with V-Discover
Experts predict a 50%-70% chance of quantum computers cracking current cryptosystems within 5 years unless the latest cryptographic controls are put in place.


Source: US National Cyber Security Strategy March 2023
Source: US National Cyber Security Strategy March 2023

Experts predict a 50%-70% chance of quantum computers cracking current cryptosystems within 5 years unless the latest cryptographic controls are put in place.


Source: US National Cyber Security Strategy March 2023

Source: US National Cyber Security Strategy March 2023

Venari Security helps regulated businesses achieve:
With the evolving technology and regulatory standards, businesses need to implement strategies to thwart potential threats and risks to comply with international privacy laws, industry regulations and data security standards.
NIST is working to publish the first set of post-quantum cryptographic standards, to be released in 2024, to protect against future, potentially adversarial, cryptanalytically-relevant quantum computer capabilities. As a result of these new standards, NIST encourages organisations to adopt cryptographic discovery tools to take inventory of their cryptographic standards.
Venari Security provides a complimentary, one-time evaluation of your organisation’s external cryptographic stance. This offers a clear view of your cryptographic vulnerabilities, the use of potentially fragile encryption, and how you measure up against benchmarks like NIST 800-52, NCSC, and other pertinent guidelines.
Cryptographic management, which is understanding and managing cryptographic keys and their usage, has traditionally been complex and requires relevant skills.
Cryptographic keys are essential for the security of data and communications. They are used to encrypt and decrypt data. If cryptographic keys are not configured or managed correctly, they can be compromised, leading to data breaches, unauthorised access, and other security incidents.
Venari Security has simplified cryptographic management by enabling organisations to understand their actively used encryption, highlight misconfigurations, reduce human errors and allow organisations to be secure and compliant.
Crypto agility is an organisation’s ability to adopt and implement new cryptographic technologies and practices in response to changing threats and risks quickly and efficiently and lower the risk of data breaches, unauthorised access, and other security incidents.
Crypto agility is particularly relevant for post-quantum as quantum computers have the potential to break many of the cryptographic algorithms that are currently in use. This means that organisations need to be able to quickly adopt and implement post-quantum cryptographic algorithms to protect their data and systems from quantum attacks.
The business landscape constantly changes, introducing new risks and opportunities. New technologies, such as the cloud and the Internet of Things (IoT), have, for example, created new security challenges. To meet these new challenges, organisations must be able to adapt their cryptographic strategies.
Various compliance regulations, including CCPA, DORA, GDPR, HIPAA, PCI, SOX, and others, have been instituted to reinforce data and privacy protections in the burgeoning digital economy.
As organisational data footprints broaden, the oversight of cryptography often remains overlooked, assessed, or scrutinised. It underscores the urgency for heightened vigilance and proactive measures in data protection strategies.
Venari Security’s technology determines how you rank across three standards: Venari Security, NIST, and NCSC. The Venari Security Standard mitigates risk to businesses and guarantees adherence to optimal security, privacy and regulatory compliance practices. The standard employs robust encryption protocols and cipher suites without known vulnerabilities.
Build trust among employees, customers, investors, and IP stakeholders by securing data in transit.
Strengthen your defenses through proactive verification.
Unlike traditional approaches relying on scattered sources like static analysis, log files, and network analytics.
Our single, holistic solution provides unprecedented visibility into actively used encryption across your enterprise integrating via API through partners to mitigate 3rd party risk.